Sign The Yum Repository
Last time we have talked about how to create a YUM repository.
openSUSE – Create your own Software Repository @ 1
If u follow the above article to create a YUM repository, it should works fine. but u will be prompted whether to accept this unsigned repository. just press YES and everything will go on without any problem.
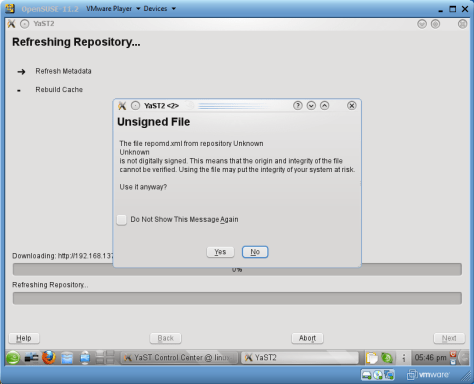
So if u don’t want to be asked everytime when u manage the packages, sign the Yum repository.
The following steps guide you how to sign the YUM repository
1. Go to the repository folder
2. Generate the key (Inputs are shown in the red squares of the picture below)
- gpg -q –gen-key
3. Try to open the a browser if it stops at (The blue square of the above picture)
- We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
4. List the keys
- gpg –list-key
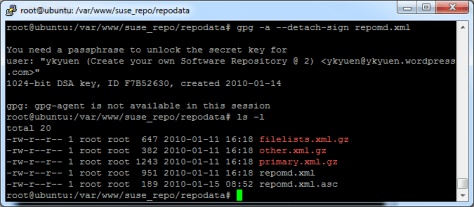
5. Make a detached signature (repomd.xml.asc) to repomd.xml
- gpg -a –detach-sign repomd.xml
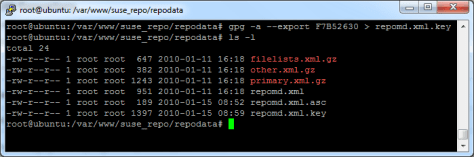
6. Export the public key to repomd.xml.key
- gpg -a –export <public_key> > repomd.xml.key
7. Import the trusted key of the repository
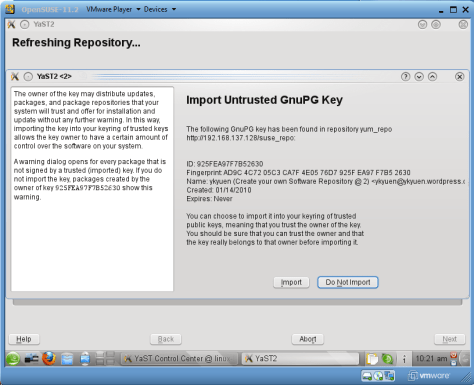
Done =)




Thanks dude… its really helpful
LikeLike
You are welcome. =D
LikeLike
Hi, I try this, but the process stops in the “blue square”
LikeLike
you need to move your mouse or type sth on the keyboard in order to generate the random bytes.
LikeLike
Thanks!
By the way, is signing the yum repo comes in additional to the .rpm file signing or instead of it?
(to support the gpgcheck=1 in the repo config file)
LikeLike
You can sign your rpm in different ways.
Signing Packages
But make sure you use the same key of your repo server to sign those packages.
You can also resign your rpm as stated in another post.
Linux – Re-sugn an rpm package
LikeLike
Hi Ykyuen,
Thanks for the answer 🙂
One more clarification – is it enough to gpg sign on the repo level for yum to trust packages,
or is it imperative to also sign individual packages?
Thanks,
Hagit
LikeLike
I think it’s not a must. but i never tried.
So if your repo is for internal used, you can leave both repo and rpm unsigned. Even if your repo is signed, you can still put an unsigned rpm there but the user who installed it has to bypass the gpg checking.
But of course, a signed repo add extra security to the rpm package and make sure no hacker have modified that rpm file.
Please correct me if i am wrong.
LikeLike
Hi,
I found the same – it seems that in order to support the gpg checking, the rpm file itself has to be signed (regardless of the repo signing).
Thanks,
Hagit
LikeLike
great~~ thanks for verifying! =)
LikeLike
Hi,
I created the local YUM repository, and signed the GPG keys as well, and was able to add the repository locally and a different machine as well using httpd. The issue is, when i search for a specific RPM, it is not listing in the client, although the RPM is present in /srv/www/htdocs/repo/RPMS repository
I am using SLES11-SP3 and my directory structure looks like this:
/srv/www/htdocs/repo/RPMS/ –
– /OL
– /SLES
– /Third-Party/ –
– jdk-7u7-linux-x64.rpm mirthconnect-3.2.1.7650.b40-linux.rpm rabbitmq-server-2.8.7-1.suse.noarch.rpm
-/repodata –
– filelists.xml.gz other.xml.gz primary.xml.gz repomd.xml repomd.xml.asc repomd.xml.key
The apache service is working great, and invoking http:///repo/RPMS/ works.
Adding the directory locally as a folder option in yast instead of httpd does add fine as well, but again it does not show RPMs.
Please Help.
LikeLike
What did u get if u enter
zypper lr?Have u checked the folder and file permissions?
LikeLike